In case you were not aware, although it appears many if not most IT security professionals know this up close and personal, SQL injections are a vector of vulnerability those with malicious intent unfortunately love to exploit. A new first-of-its-kind study by security research firm Ponemon Institute, done in conjunction with DB Networks, a provider of behavioral analysis database security solutions, is out and deserves to be on your “must read” list.
Titled, “The SQL Injection Threat Study,” today announced the results of the Ponemon Institute’s first-of-its-kind SQL injection threat study. The study was based on recent research aimed at determining the challenges facing organizations around the pervasiveness of SQL injection attacks, and opinions on how to stop these threats. It analyzed responses from 595 IT security practitioners in the United States working across a broad spectrum of industries and also the public sector with fifty-nine percent of respondents working for organizations with 5,000 or more employees.
The reason this is an important report can be seen in the top-level findings which certainly will give IT professionals pause:
- 65 percent of respondents had experienced SQL injection attacks that successfully evaded their perimeter defenses in the past 12 months.
- Each SQL injection breach took an average of nearly 140 days to discover
- Each breach required an additional 68 days on average to remediate.
Before getting to additional findings a quick primer on SQL injection is in order.
SQL is the extremely popular special-purpose programming language designed for managing data held in a relational database management system (RDBMS). SQL injections involve the insertion of malicious SQL statements into an entry field for execution (e.g. to dump the database contents to the attacker). As the report explains, “They exploit security vulnerabilities in an application’s software. SQL injection is most commonly known as an attack vector through public facing websites but can be used to attack SQL databases in a variety of ways.”
In short, SQL injections are really nasty stuff, and popular with the bad guys. They are hard to detect as well as both time-consuming and costly to remediate.
It’s a bad situation
“We believe this is the first study to survey the risks and remedies regarding SQL injection attacks, and the results are very revealing,” said Dr. Larry Ponemon, founder and chairman of the Ponemon Institute. “It is commonly accepted that organizations believe they struggle with SQL injection vulnerabilities, and almost half of the respondents said the SQL injection threat facing their organization is very significant, but this study examines much deeper issues. For example, only a third of those surveyed (34 percent) agreed or strongly agreed that their organization presently had the technology or tools to quickly detect SQL injection attacks. And more than half (52 percent) of respondents indicated that they don’t test or validate any third party software to ensure it’s not vulnerable to SQL injection.”
The report is filled with a series of interesting findings. One intriguing chart that hopefully entices you to download the full report is below. It speaks for itself.
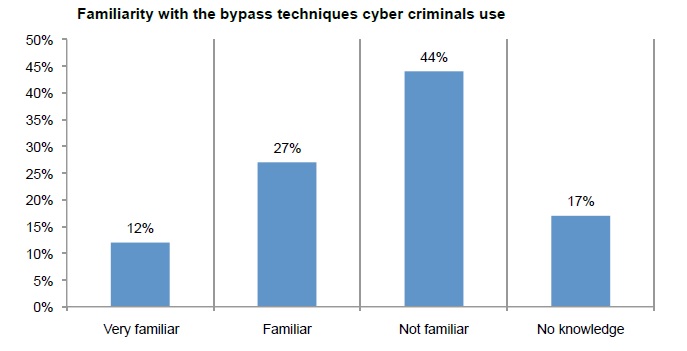
Source: Ponemon Institute and DB Networks report, The SQL Injection Threat Study
Additional key findings of the study include:
- Nearly half (46 percent) were familiar with the term “WAF Bypass.”
- 56 percent agreed or strongly agreed that determining the root cause of SQL injection is becoming more difficult because of the trend for employees to use their personally owned mobile devices in the workplace (BYOD).
- 52 percent of respondents indicated that they don’t test or validate any third party software to ensure it’s not vulnerable to SQL injection.
- 44 percent utilize professional penetration testers to identify vulnerabilities in their IT systems; but only a third (35 percent) of those penetration tests included testing for SQL injection vulnerabilities.
- 88 percent of respondents had a favorable or very favorable opinion of the use of behavioral analysis technology for detecting SQL injection attacks.
- 52 percent indicated they either had begun replacing or would be replacing their signature-based IT security systems with behavioral analysis based IT security systems within the next 24 months.
- 49 percent said they would be using behavioral analysis based systems specifically for database transaction security.
“It’s well known that SQL injection attacks are rampant and have proven to be devastating to organization of all sizes,” said Brett Helm, Chairman and CEO of DB Networks. “This study delves into both the scope and many of the root causes of SQL injection breaches. Signature-based perimeter defenses simply cannot keep up with the sophistication of today’s complex SQL injection attacks. It’s interesting that this study indicates security professionals are now recognizing this and overwhelmingly had a favorable opinion of applying behavioral analysis technologies to address the SQL injection threat.”
It has become almost a cliché at this point that authentication/identity is the new perimeter. The barbarians have figured out how to bypass the gate and are inside creating mischief. The silver lining in this report is that IT, in the face of BYOD creating even more complications for assuring apps as they continue to proliferate on devices behind traditional security measures, have taken to heart the severity of the threat posed by SQL injections and are looking to behavioral analysis technology as a valuable tool for keeping those with malicious intent from wreaking havoc.
This is an instance where what you don’t know can and will hurt you, and having better visibility into SQL activities so problems can be determined quickly and preventive measure can be taken sooner rather than later is an important step to take as part of best practices to reduce vulnerability risks
Edited by
Maurice Nagle